
Pin on MODA

TREND FOCUS: THE BELT BAG — Petite and Bold
English-to-Anglish-Dictionary/dictionary.json at master · trosel/English-to-Anglish-Dictionary · GitHub
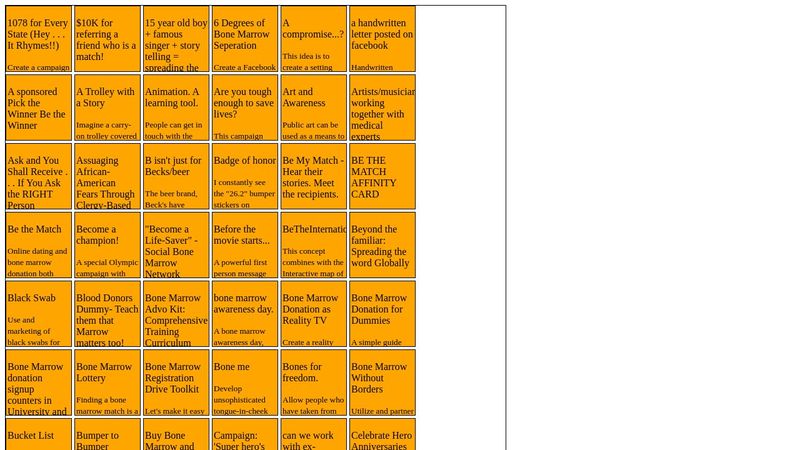
bonemarrow-baseline

APT40: Examining a China-Nexus Espionage Actor - vulnerability database
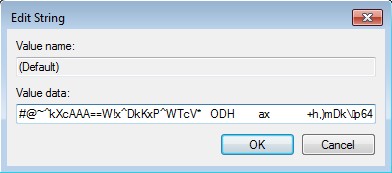
POWELIKS — A Persistent Windows Malware Without Any Installe - vulnerability database

APT40: Examining a China-Nexus Espionage Actor - vulnerability database
chain-analysis/twitter_names.json at master · martinjc/chain-analysis · GitHub

11 Best Belt Bags Under $40 That Are Also Super Stylish - theFashionSpot

Microsoft Windows Common Controls MSCOMCTL.OCX Vulnerability - exploit database
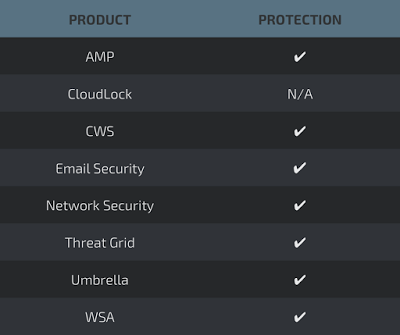
When combining exploits for added effect goes wrong - vulnerability database

How RTF malware evades static signature-based detection - vulnerability database
When combining exploits for added effect goes wrong - vulnerability database
