
Cell Tower AM Detuning Facts for Compliance and RF Safety
Cisco Talos Honeypot Analysis Reveals Rise in Attacks on Elas - vulnerability database

Imperva's Top 10 Blogs of 2017 - vulnerability database

Our Demo at Zabars & Dinner at a Wonderful Friend's Home — Real Baking with Rose

Our Demo at Zabars & Dinner at a Wonderful Friend's Home — Real Baking with Rose

Penn State Students react to closure of 'staple' Gumby's Pizza, Penn State, State College News

How the Rise of Cryptocurrencies Is Shaping the Cyber Crime - vulnerability database

World Turn'd Upside Down: Secret Life of Bloggers Blog Party Post
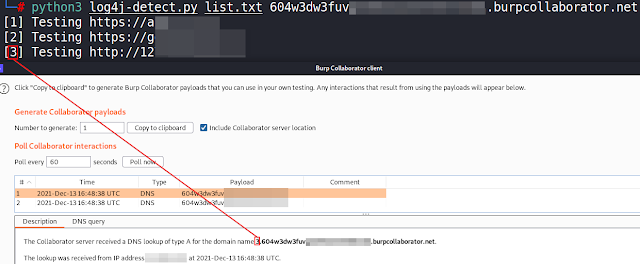
Log4J-Detect - Script To Detect The Log4j Java Library Vul - vulnerability database

Grilled Stickies - Centre County Encyclopedia of History & Culture

APT review: what the world's threat actors got up to in 2019 - blog database

Sound, Fury, And Nothing One Year After Equifax - vulnerability database

Ukraine-Russia Cyber Warzone Splits Cyber Underground - vulnerability database
