
Storing Two-Factor Codes - Enterprise Guide

Simplify Two-Factor Authentication For Customers
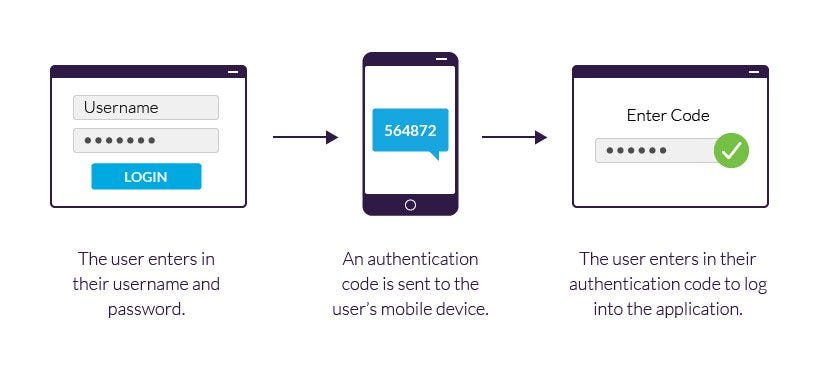
Step-by-Step Guide to Implementing Two-Factor Authentication with Node.js, by Adarsh Dayanand
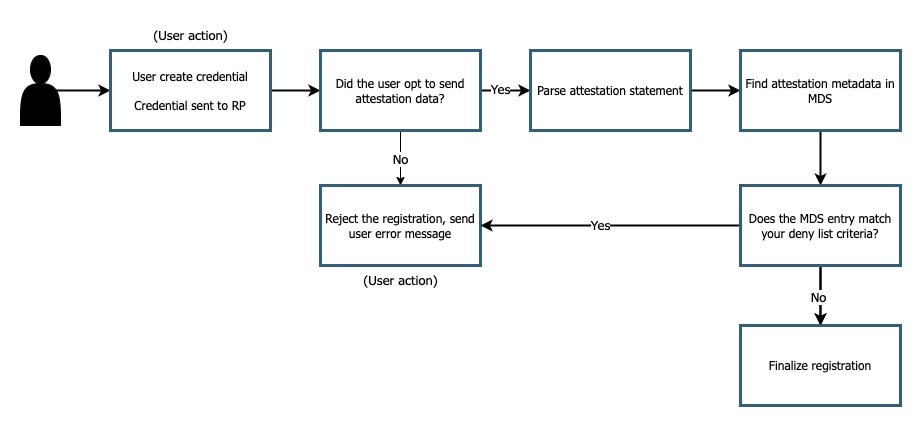
Authenticator Management
Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey
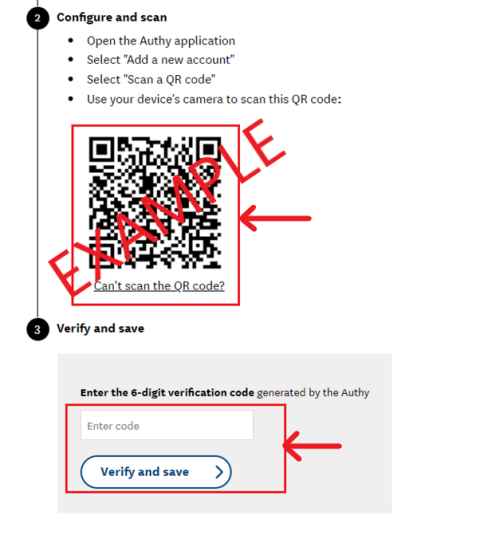
Activate, use and manage the Google Authenticator app - The University of Auckland

How to use an authenticator app for 2FA on iOS - SecureMac
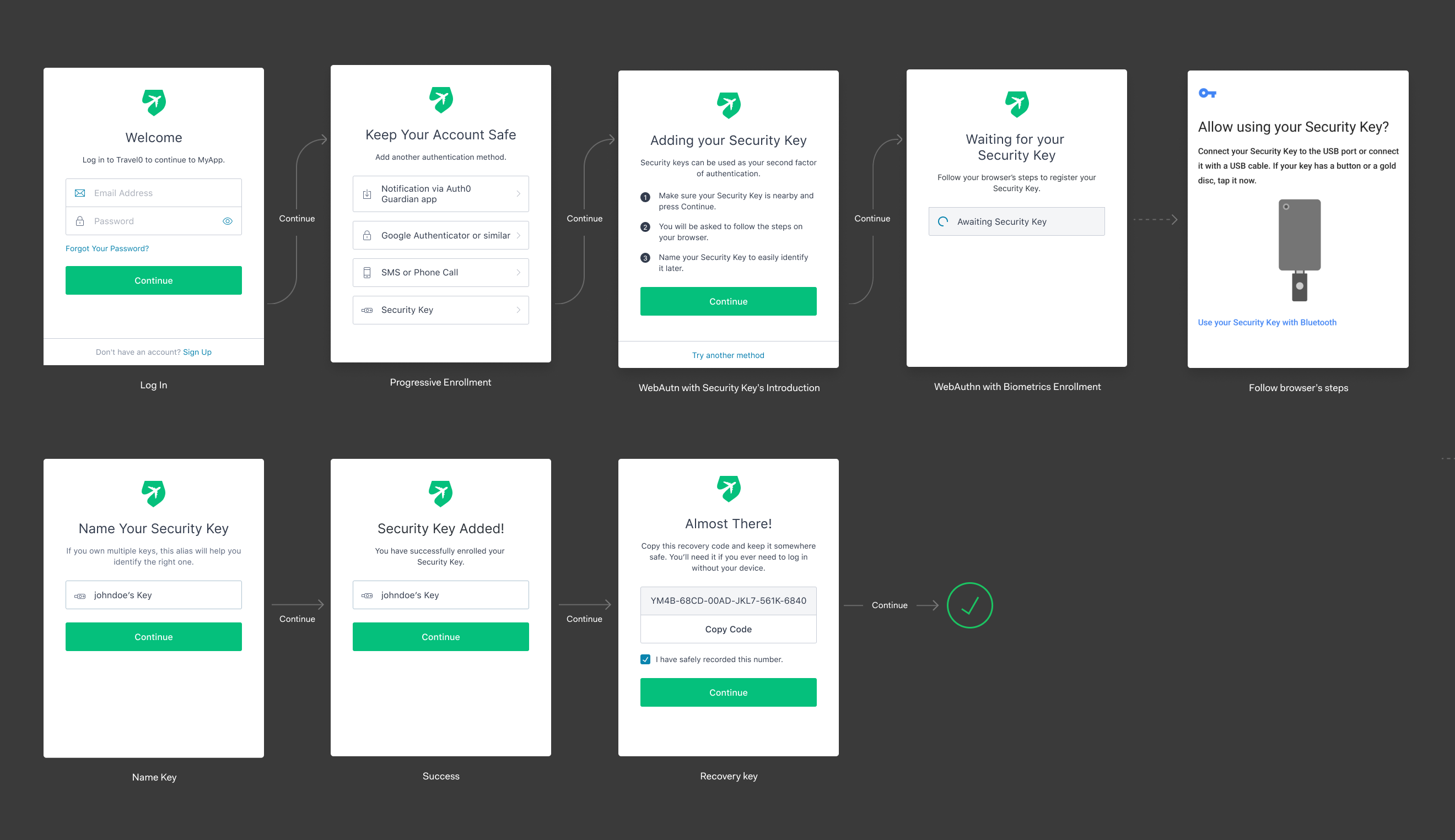
FIDO Authentication with WebAuthn
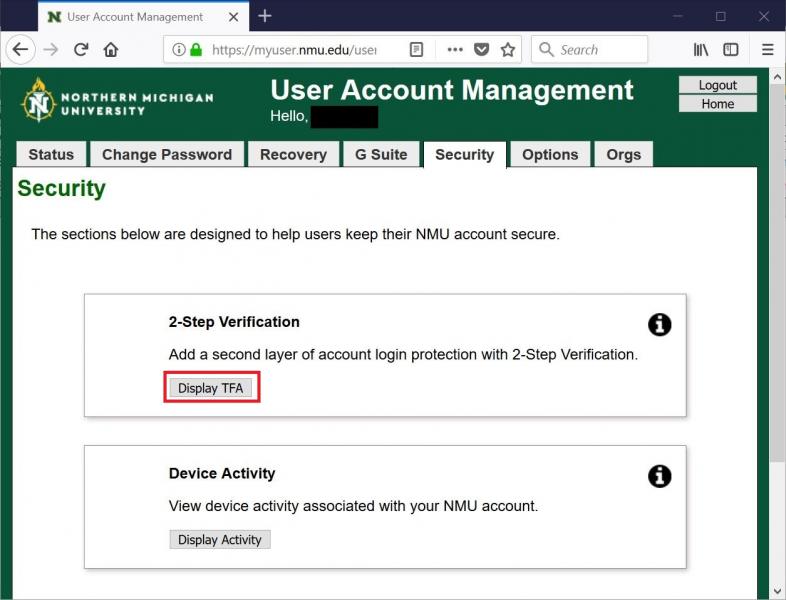
Using Google Authenticator for 2 factor authentication

WordPress Two-Factor Authentication Guide - WPZOOM
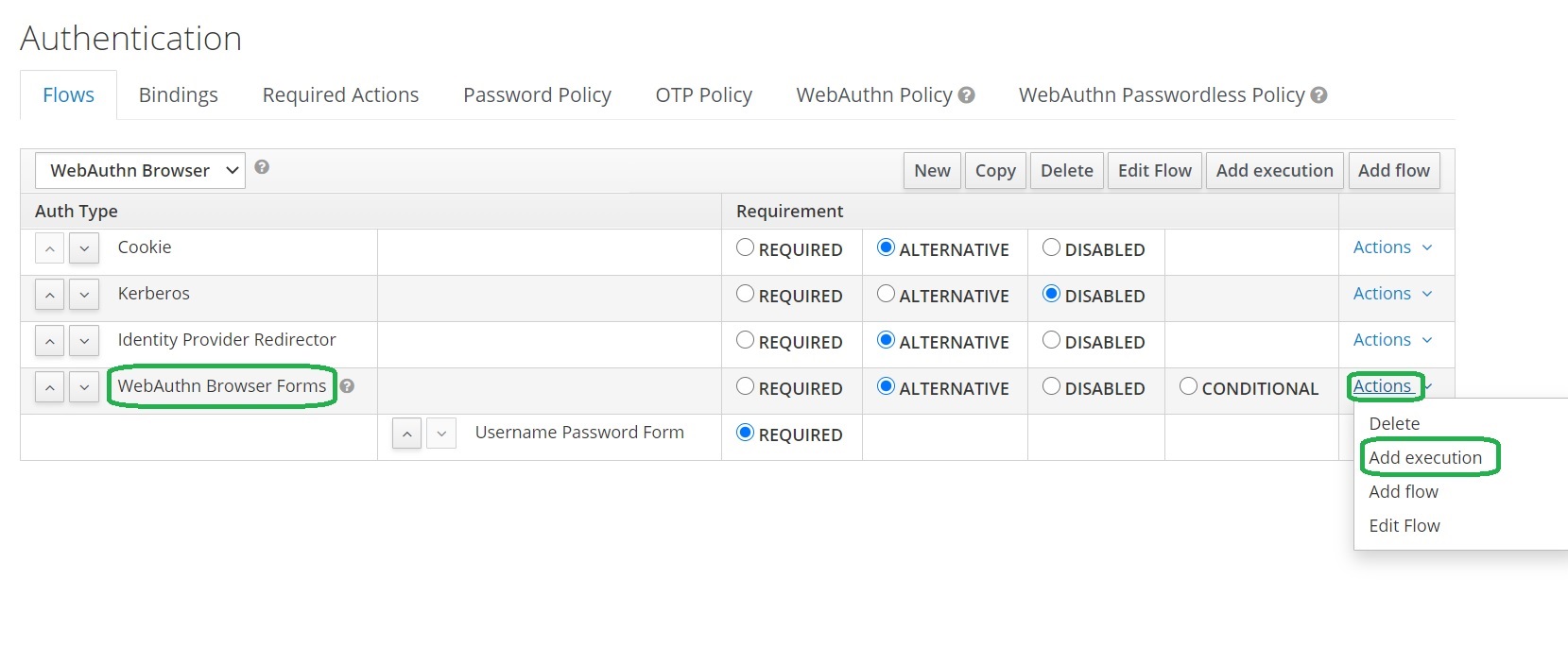
Two-Factor Authentication with Keycloak WebAuth · Ultimate Security Professional Blog

Authentification Guide — Two authenticators
How to set up the Two-Step Authorization (Google Authenticator). – Gaijin Support
Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey
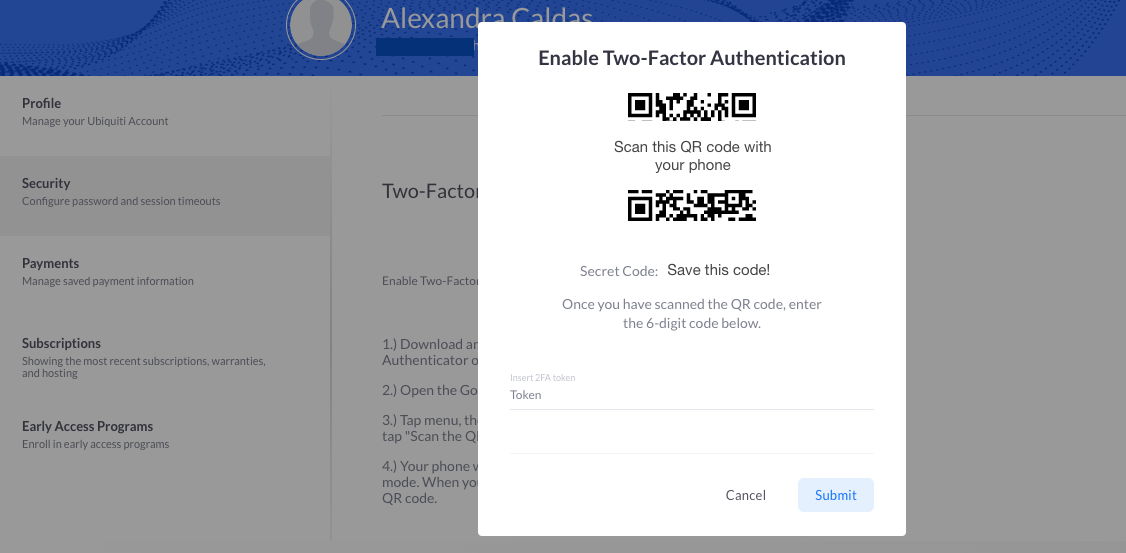
Token2, Classic OATH hardware tokens for Office 365, Hardware token for Ubiquiti Account 2FA, TOKEN2 MFA Products and Services
