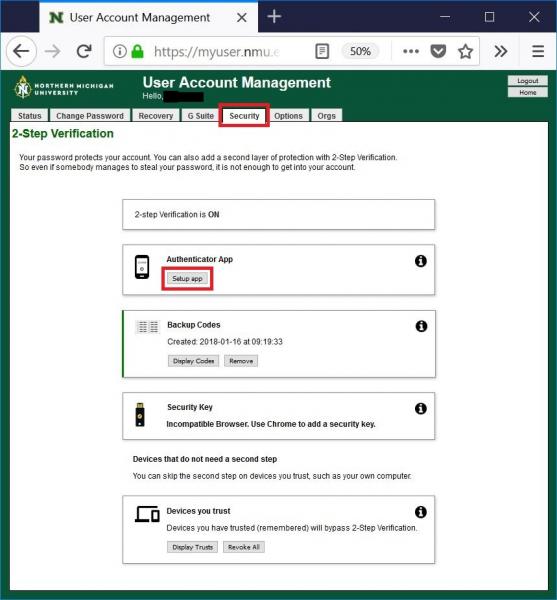
Using Google Authenticator for 2 factor authentication
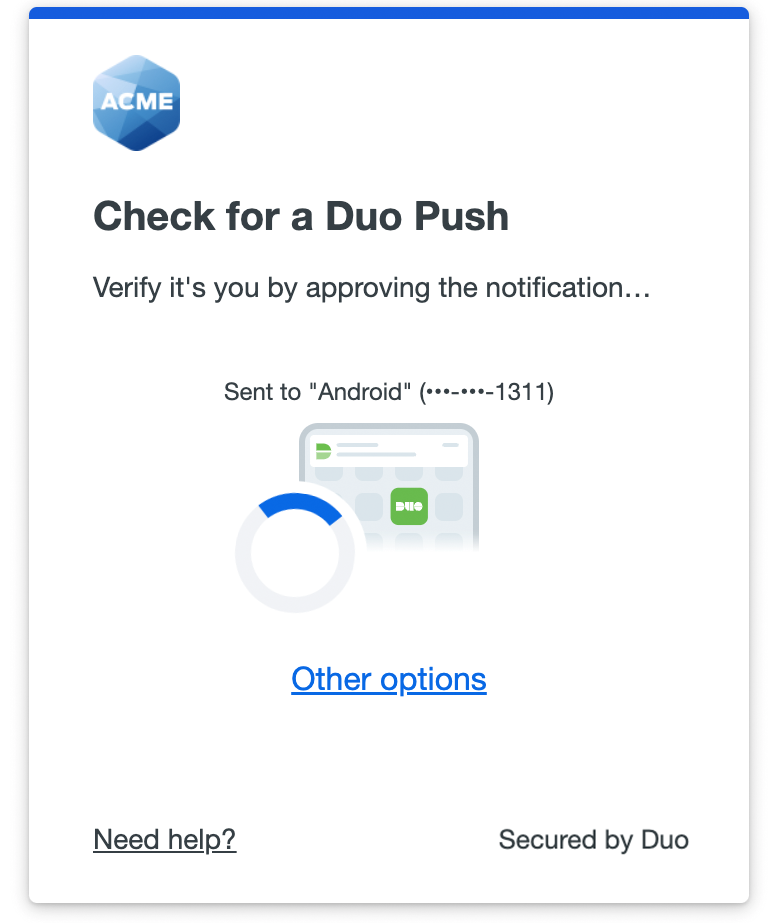
Use Security Keys with the Traditional Duo Prompt - Guide to Two-Factor Authentication · Duo Security

Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey
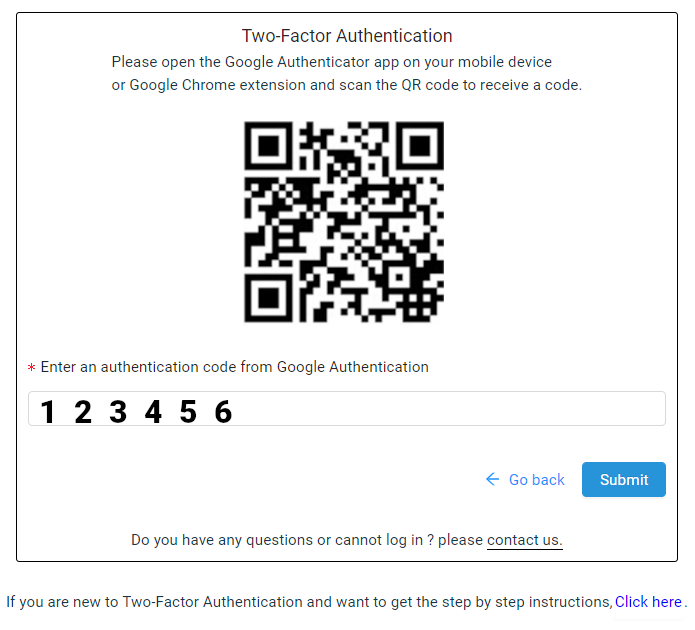
Two-Factor Authentication
Two-factor authentication (2FA) (user guide) – Miro Help Center

Two authenticators
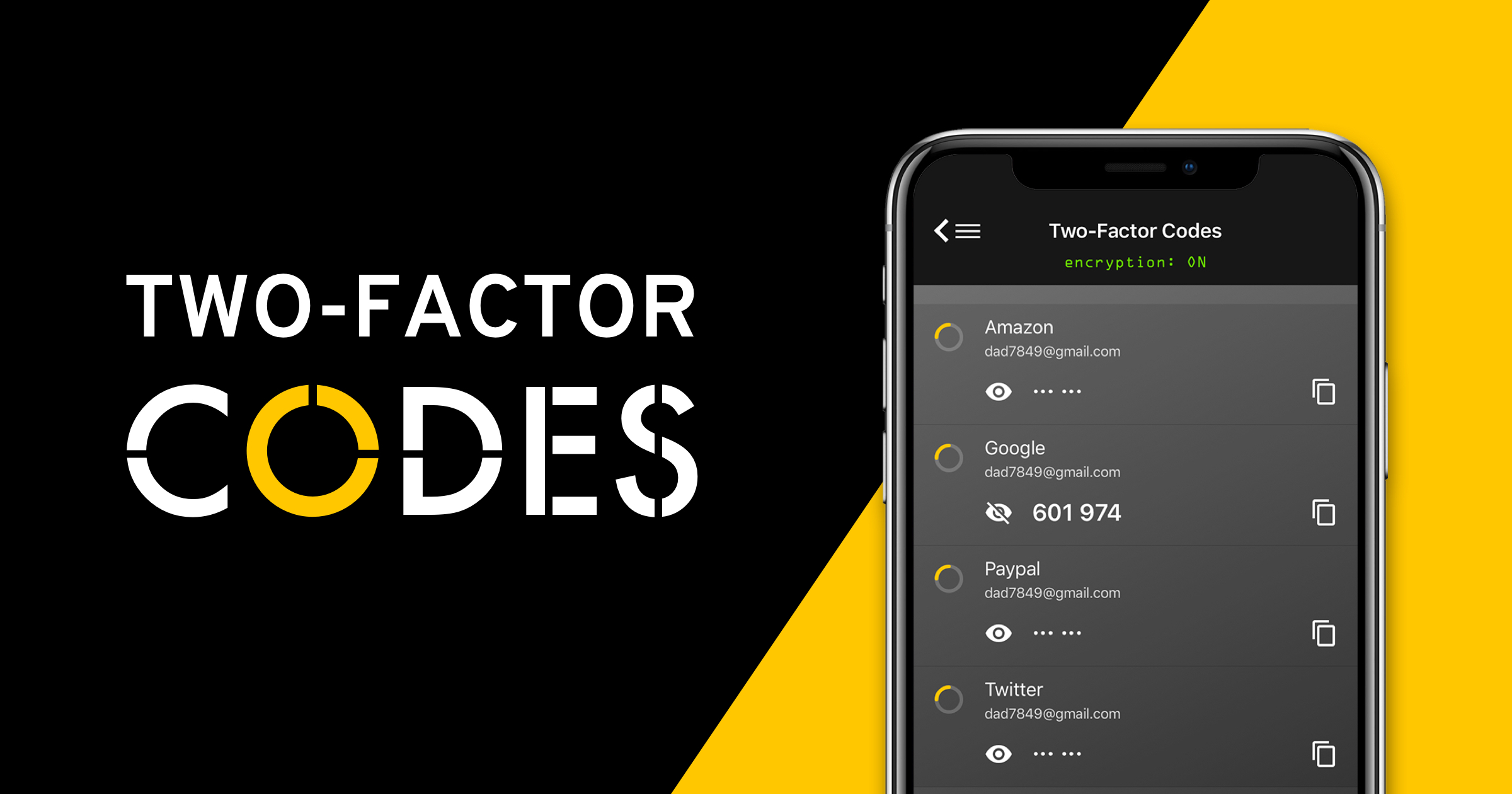
Integrated Two-Factor Authentication (2FA) Codes with Keeper
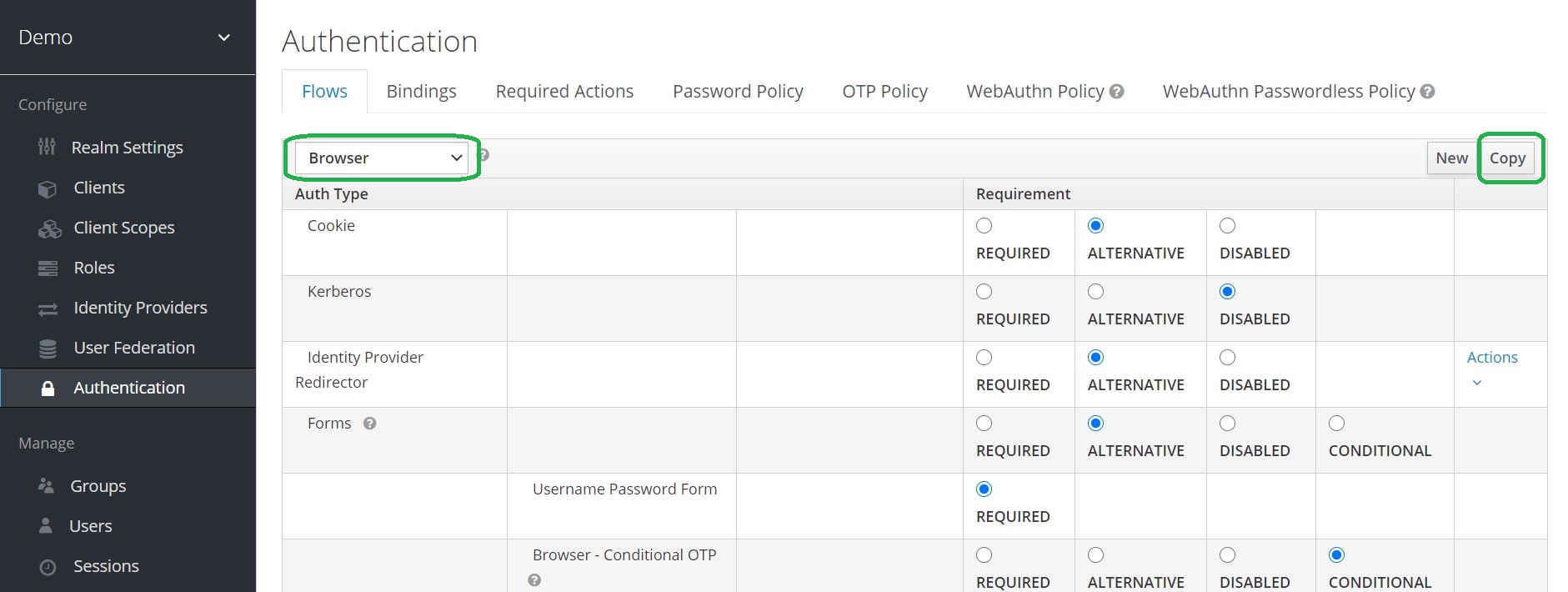
Two-Factor Authentication with Keycloak WebAuth · Ultimate Security Professional Blog

Using Kerberos for Authentication Relay Attacks - vulnerability database

Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey
Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey
Turn on two-factor authentication
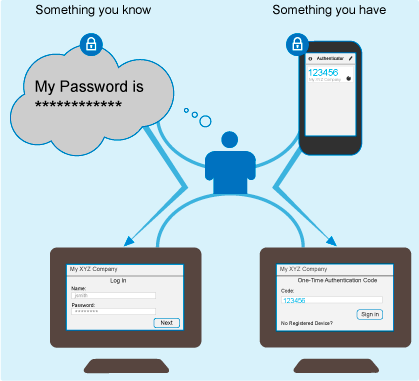
Configuring the Time-Based One-Time Password (TOTP) Tool for Two-Factor Authentication Using Google Authenticator - NetIQ® CloudAccess and MobileAccess Installation and Configuration Guide

Client to Authenticator Protocol (CTAP)
Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey
